
Vulnerability Management
Vulnerability management is one of the fundamental proactive cyber security services. Identifies weaknesses in IT systems and infrastructure to minimise the risk of successful cyber attacks.
Vulnerability management is one of the fundamental proactive cyber security services.
At Axians, we run an extensive vulnerability management team with rich history of providing top-notch solutions in the cybersecurity landscape. With a wealth of experience catering to large enterprises, our dedicated team is committed to safeguarding your business against potential threats and vulnerabilities.
We understand the intricate challenges that businesses and organizations face in today’s ever-evolving digital landscape, and our proven track record speaks volumes about our ability to deliver comprehensive vulnerability management solutions that meet the unique needs of our clients.
What can we help you with?
-
Vulnerability Management Scanning Platform
With a focus on real-time threat detection and swift response, we ensure that your organization and digital assets remain secure.
-
Vulnerability Management Process and Remediation
Get an overview of how vulnerabilities are addressed, when and by whom, including an overview of approved exceptions.
-
Vulnerability Management Light
Vulnerability Management Light is specifically designed for small and medium-sized organisations and carries a minimal cost.
Your benefits with Axians
Vulnerability Management Scanning Platform
Experience proactive protection with our comprehensive Vulnerability Management Scanning Platform service. Our experts specialize in the seamless deployment and operation of cutting-edge vulnerability management tools, specifically designed to cater to the unique needs of medium and large-scale organizations. With a focus on real-time threat detection and swift response, our Qualys-based solution ensures that your digital assets remain secure, and your organization stays ahead of potential vulnerabilities.
Axians offers both support services and professional services on top of Qualys platform. With support services, you get the access to L1/L2/L3 experts that will be responsible to operate and housekeeping your VM environment and to deliver the requested scan results. On the other hand, professional services provide Qualys optimisation, automation, and integration projects delivered by our top Qualys experts. Apart from Qualys, we are able to support you on other scanning platforms (e.g., Nessus, Rapid7, etc.).

Product list
Vulnerability Management Scanning Platform
Read a summary of our vulnerability scanning platform offerings
Vulnerability Management Process and Remediation
Take control of your cybersecurity posture with our Vulnerability Management Process and Remediation service. We work closely with your organization to establish robust vulnerability management processes and execute them flawlessly. Tailored to the requirements of medium and large-scale enterprises, this service empowers you to identify, prioritize, and address vulnerabilities effectively, minimizing risk and fortifying your digital infrastructure against potential threats. Get the insight into how vulnerabilities are addressed, when, and by whom, including the visibility of approved exceptions.
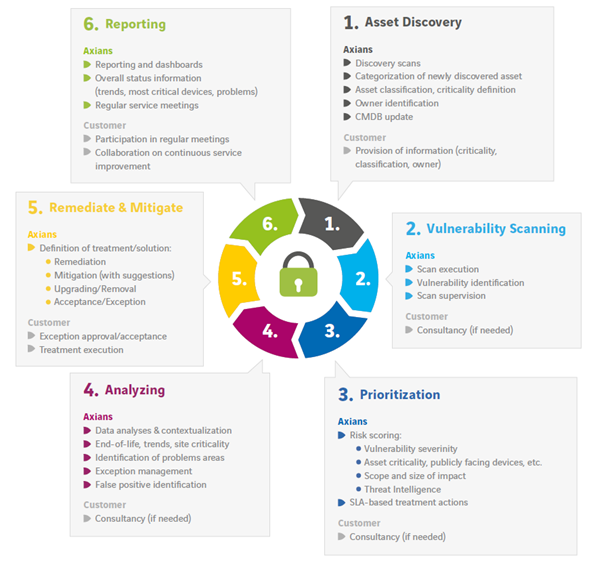
Vulnerability Management Process and Remediation is a follow-up service for technical vulnerability scanning, mostly implemented as a technical tool like Qualys, Nessus, Rapid7, or others. The focus areas are Prioritization, Analysis, Remediation and Mitigation, and Reporting phases of Vulnerability Management cycle. The two deliverables out of this service are:
- Setting, description, and implementation of VM processes adjusted for the customer
- Ongoing activities executed by Vulnerability Analyst role

Product list
Vulnerability Management Process and Remediation
Download a free compact summary of key information on the vulnerability management and remediation process
Vulnerability Management Light
Empower your small or medium-sized organization with Vulnerability Management Light, a hassle-free solution that delivers regular vulnerability scanning and streamlined result processing.
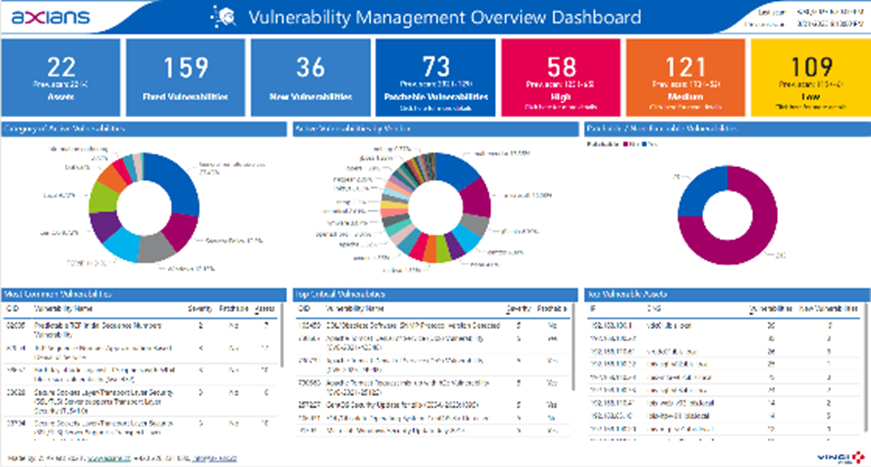
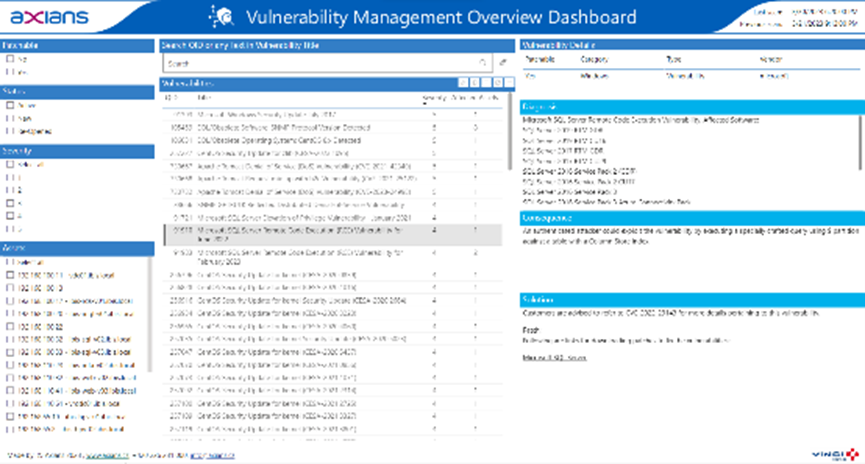
Say goodbye to the complexities of purchasing licenses – our offering includes an intuitive Power BI Dashboard that provides actionable insights from your vulnerability scans that are executed regularly by our experts. Stay informed and in control of your cybersecurity efforts without the overhead, making vulnerability management seamless and efficient.

Product list
Vulnerability Management Light
Download a free compact summary of key information about Vulnerability Management Light.
How can we help you?
Do you have a project? A question? Are you interested in our solution? Contact our experts and we will get back to you as soon as possible.
Contact
Contact us! We will answer as soon as possible.

