Security Assessment and Strategy
Risk unveiled, strategy revealed: crafting your robust cybersecurity defense
Elevate your cybersecurity with a health assessment and follow-up strategy
Our Security Assessment and Strategy service offers your organization a comprehensive, high-level cybersecurity evaluation across critical dimensions. We specialize in providing cutting-edge IT and technology solutions to businesses and organizations, ensuring that your digital assets are shielded with the utmost vigilance. A 360-degree cybersecurity evaluation spans five key domains, each pivotal to your organization’s cybersecurity posture.
Key areas:
Your benefits with Axians
The outcome of the service is not only the evaluation of current situation, Axians provides you with a high-level security strategy meticulously crafted to suit your organization’s needs. We guide you through the intricate terrain of cybersecurity, suggesting the next pivotal steps to enhance your digital defense.
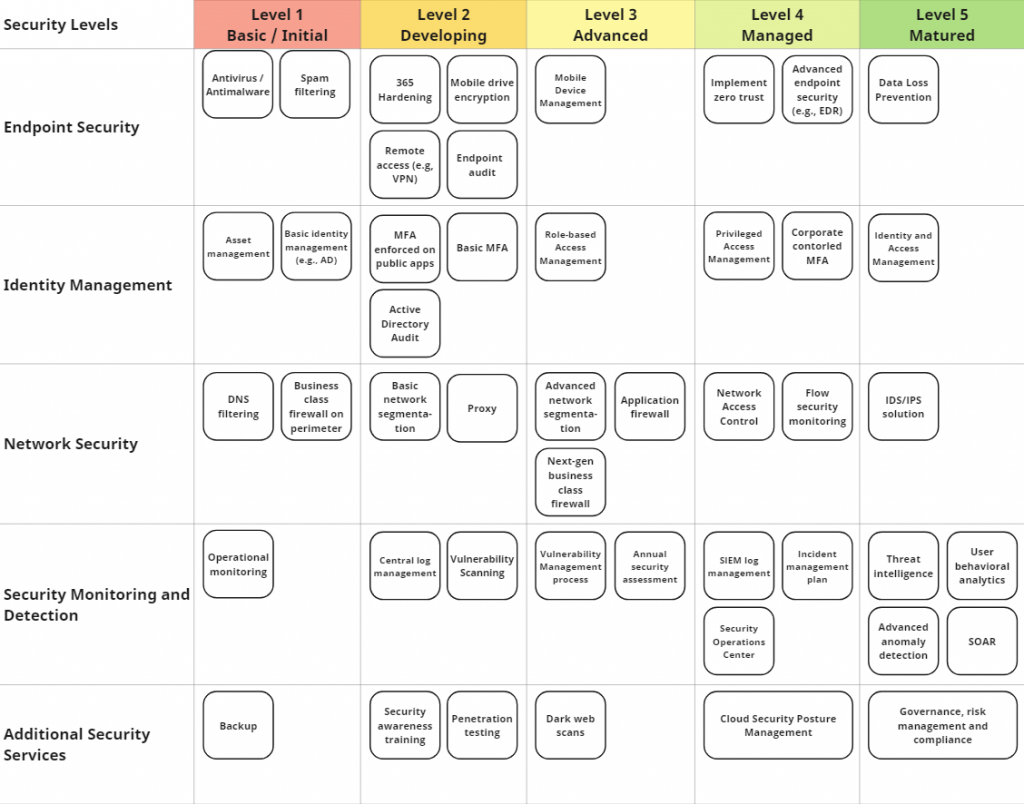
Axians Cybersecurity Maturity Model
Our proprietary cybersecurity maturity model spans five distinct security levels, a structured continuum from foundational protection to advanced resilience. This model, encompassing the same five areas of evaluation, serves as our guiding compass throughout the assessment process. Not only does it illuminate your current standing, but it also charts the course for your progression towards a fortified cybersecurity stance.
At Axians, we adhere to the highest industry benchmarks.
We supplement our methodology with globally recognized security standards such as the NIST SP-800 series and ISO/IEC 27000 series. This synthesis of expertise and standards ensures a holistic evaluation and strategic direction that stands strong against the most intricate threats.
How can we help you?
Do you have a project? A question? Are you interested in our solution? Contact our experts and we will get back to you as soon as possible.
Contact
Contact us! We will answer as soon as possible.