Today, no one doubts that cyber-attacks represent a significant risk for organizations, which must be reckoned with and defended against. Recent media cases include the attack on Twitter.
During this incident attackers managed to gain access to internal tools and subsequently take over some popular accounts. Ransomware attacks are also relatively common, in which data is encrypted and a ransom is required. A recent victim was, for example, Garmin. Attacks of this type are not avoided even in the Czech environment, we can remember the attacks on hospitals and industrial enterprises in 2019 and 2020. At the end of 2020, attacks carried out through a compromised supply chain – malware in the SolarWinds Orion software update – received a lot of media attention. In this article, we will take a closer look at the course of such targeted “hacker” attacks.
In general, cyber-attacks target breaches of confidentiality, integrity, or availability. A breach of confidentiality means that an attacker gains access to sensitive company data, whether it is internal documents or customer data. When integrity is compromised, an attacker changes stored data, such as user permissions, account balance, or deletes files. If the availability is violated, the information system is out of operation for a certain period.
The specific form of the attack and its target depends primarily on who the attacker is. We can divide them into several groups according to various aspects:
- Beginners (script kiddies) – these are attackers without greater technical knowledge who use tools freely available on the Internet. Attacks can involve scanning publicly available services and known vulnerabilities or guessing credentials. These attackers tend to be motivated by curiosity, the pursuit of experience or recognition of their surroundings.
- Activists (hacktivists) – tend to be politically motivated and seek visibility. Their attacks often involve the coordinated congestion and temporary shutdown of a website belonging to government or corporation. In more sophisticated attacks, the content of websites may be altered or sensitive information may be obtained.
- Cybercriminals – they are about gaining financial gain. For example, they can install ransomware, gain access to Internet banking or credit card numbers, use the power of the compromised computer to extract cryptocurrencies, or connect the computer to a botnet (a network of controlled devices attacking other targets). Attacks are often untargeted and aimed for a large number of users. They are then successful in only a small number of them, but recently more sophisticated attacks targeting specific organizations such as hospitals have gotten more frequent.
- Internal insiders – these attackers know and have access to the organization’s internal network. It can be a dissatisfied employee or even a former employee whose remote access has not been cancelled. This attacker may seek revenge or personal gain resulting, for example, from passing internal documents to competitors.
- State-sponsored attackers – this includes various professional hacker groups that are believed to be controlled by different states and engaged in espionage. This type of threat is often referred to as APT (advanced persistent threat), ie attackers using precisely targeted attacks and advanced techniques such as zero-day vulnerabilities, ie publicly unknown vulnerabilities in systems. These attackers can move around the infected networks for a long time without being detected and to obtain sensitive information. Defence against these types of attacks is very complex, however, these attackers focus primarily on strategically interesting targets.
Sophisticated attacks consist of several consecutive phases. These phases can take place automatically as in the case of ransomware attacks (the combination of malware Emotet-TrickBot-Ryuk responsible for attacks on Czech hospitals), or they can be partially controlled manually as in the case of APT attacks. The individual phases of the attack are described for example, by the Cyber kill chain or Miter ATT & CK methodology, which also provides a database containing an overview of attack techniques used by various malware or APT groups. Further in this article, we will describe the main steps of a cyber attack, such as a ransomware attack or a targeted hacker attack, without going into too much technical detail.
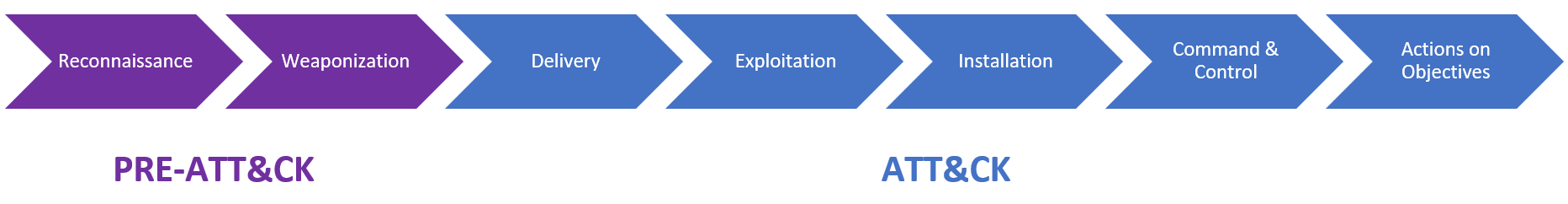
Research and preparation
Before the attacker launches an attack, he chooses his target and finds out as much relevant information about it as possible. Attackers can target a specific organization or a specific vulnerability, such as missing security patch on a server. If an attacker chooses a specific company, he is often able to find out a lot of information about it on the Internet, which can help him in carrying out the attack, such as email addresses and other contacts to employees, server addresses or technologies used. The attacker scans the devices and services available from the Internet for known vulnerabilities. The attacker could also customize malicious code (malware) for a specific attack.
Initial access
For an attacker to be able to launch attacks on a system, the system must be reachable to him so he can connect to it. Interesting systems containing sensitive information are often located in a local network and are not directly accessible from the Internet or the connection is possible only after entering the login data. An attacker can overcome this problem in several ways.
First, it can find vulnerabilities on any interface available from the Internet, such as firewall, email server, or redirected port vulnerabilities. However, this vector of attack on the internal network is rather rare, because the elements on the perimeter of the network are often sufficiently secured, resp. existing vulnerabilities do not allow access to the internal network.
Additionally, an attacker could try to guess the credentials to connect to a VPN, remote desktop, e-mail, or other remotely accessible application. The attack is easy if the default credentials are left for a service or a user uses a very weak password. The defence against password testing consists of blocking the account after several unsuccessful attempts. However, this measure does not have to stop the attacker. When using the password spraying attack technique, the attacker first detects a large number of usernames (typically email addresses) and tries a few popular passwords for each (eg Leto2020), thus avoiding account suspension. An attacker could also try pairs of usernames and passwords leaked from some other service (so-called credential stuffing). If one of the users uses the same password, the attacker has won.
An attacker could also attack a typically weakest security link – a user – and simply cunningly ask for access. Attacks involving elements of social engineering include phishing, ie an attack conducted through sending an e-mail. An attacker here tries to persuade the user to run the attached file (eg allegedly unpaid invoices) or enter login details on a fraudulent site. It is enough if the attacker has caught one user. A targeted phishing attack with content tailored to a particular user is called spear phishing. There are also targeted phishing attacks via phone, so-called vishing (this technique was used in the attack on Twitter).
Attacks conducted through a compromised supplier can have a critical impact. Many vendors may have access to other companies’ internal networks for support and remote administration. If a successful attack on a vendor occurs, an attacker could gain access to these other networks. Alternatively, an attacker could compromise the process of developing and distributing software updates and add their malicious code to a new version of the software, as has happened to SolarWinds.
Code execution
When an attacker forces the user to run a malicious file, he gains access to that user’s computer. This malicious file can be for example, an executable binary file, a script, and macros in MS Office files are often used for this purpose.
The executable code typically connects to the attacker’s server and downloads additional instructions and modules. Because the running file does not contain malicious code directly, but only instructions for downloading it, a simple anti-virus scan might not discover it. However, attackers use other methods to avoid detection or distract the user (such as using encryption or running code directly in memory).
Escalation of privileges and persistence
The executable code runs with the privileges of the user who executed it, which may not be the administrator. However, to perform other attacks, an attacker often needs administrator privileges on the computer. For this purpose, it is possible to use various known vulnerabilities in the operating system, or errors in its configuration, allowing the escalation of privileges. This sub-step makes it easier if the operating system is not updated regularly.
For an attacker to retain control even after restarting the computer, he can use one of the techniques to achieve so-called persistence. For example, adding the process to start the program automatically when the computer is turned on, creating a new service or scheduled task, creating a new user account, or manipulating another process.
Obtaining access data
A step that can allow other devices and services to be compromised is to obtain credentials stored on the controlled computer. With administrator privileges on the computer, it is possible to obtain fingerprints (hashes) of Windows (and Linux) credential passwords. This includes other users who have logged on to the computer. In some cases, the user password can be obtained directly.
An attacker could also detect passwords stored in a Web browser or intercept keystrokes to gain additional credentials.
Network distribution
In the next step, the attacker finds out what other devices and services the controlled computer has access to and looks for some known vulnerabilities that he could exploit. It also finds out where he can log in with the obtained login data. For example, if an attacker can determine the credentials of a local administrator and this information is valid on other devices, he can also control it (for example, through Remote Desktop or SMB protocol for file sharing). An attacker on other devices, where he manages to gain access, repeats some of the above steps until he reaches his target. In a Windows domain, such a typical target is a domain controller that contains user records and, when controlled, gives an attacker virtually unrestricted access to computers and servers on the network.
The ultimate target of the attack
Once an attacker gains sufficient control over devices on the network, he can proceed to the final step of the attack. It can collect sensitive information and send it unnoticed to its server. The attacker then sweeps traces of his presence, he can also leave a so-called backdoor in the system, which will allow him to re-access in the future. Alternatively, an attacker could appear on the network unnoticed for an extended period (as in the case of APT).
It is possible to run ransomware that will encrypt selected data (including backups) and a ransom is required.
DEFENSE AGAINST ATTACKS
Effective defence against sophisticated targeted attacks requires more complementary measures that cover all of the outlined phases of the attack. These can be, for example, the following technical and non-technical measures:
- Regular training of users in the field of computer security
- Protection of emails (antispam) and user stations (antivirus)
- Password policy (sufficient complexity, not using same passwords), multifactor authentication, privileged account management (PAM)
- Regular system update (patch management)
- Network segmentation, access restriction (firewall)
- Regular scanning of known vulnerabilities
- Monitoring and logging (centralized system – SIEM, security team – SOC)
- Sensitive data protection (DLP)
The measures taken should target the specific risks relevant to the organization. It is thus necessary to know your information systems, infrastructure and their possible vulnerabilities.
Penetration tests, which simulate a real cyber-attack or certain parts of it, are invaluable for detecting security flaws. For example, penetration tests can target systems available from the Internet (external tests), systems on the internal network (internal tests), a specific web application from the position of regular users, or employees (simulated phishing campaign). Compared to the damage that a real attack could do, penetration testing has no adverse effects on the organization’s operations.
The security of information systems should not be underestimated, as increasingly sophisticated attacks are taking place. It is advisable to consult with experts, such as we are here at Axians. We offer a full portfolio of services from risk analysis and design of security measures to the implementation of penetration tests.


